趨勢科技
對應日前WannaCry勒索軟體的橫行與威脅,已有不少資安廠商也提供建議與相關資訊供參考。而為了快速地找到公司內未修補MS17-010的電腦,我們看到有資訊人員提供,利用Nmap網路掃描與探測工具,自發性地製作一個檢測範本script(smb-vuln-ms17-010.nse),以協助網管人員來檢測。
這種方式對於企業網管人員而言應有一定的幫助,可以一次大量檢查內部網路多臺電腦的狀態,而檢查200臺電腦大約也只要10秒鐘。
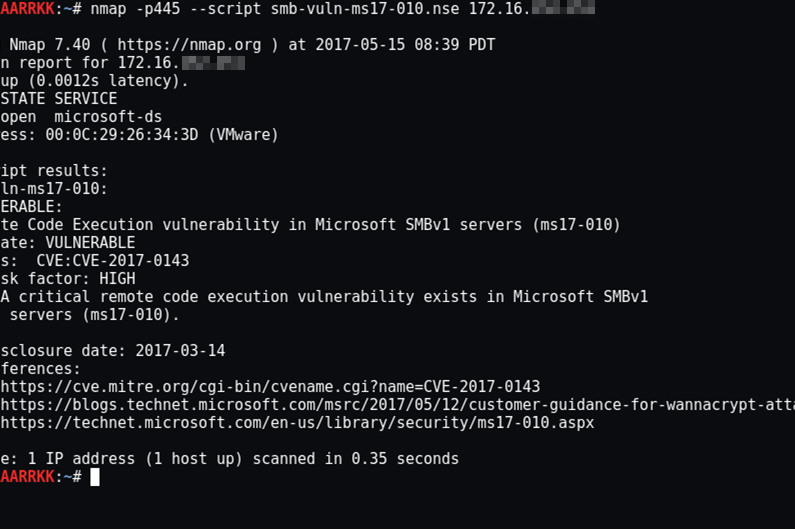
步驟上也不算太複雜:一、到nmap.org 下載 nmap.exe (有windows版)並安裝,二、將smb-vuln-ms17-010.nse丟到nmap\script目錄下(相關smb-vuln-ms17-010.nse範本,請參考最下方內容),三、鍵入:nmap -p 445 --script smb-vuln-ms17-010 ip-range
此外,為簡化了個人使用者的預防工作,防毒大廠趨勢科技現在也免費推出了的WannaCry漏洞檢查工具(Trend Micro WCRY Simple Patch Validation Tool)。點擊前往官方連結
趨勢表示,此工具可以幫個人使用者在windows電腦上執行以下兩項工作,首先是檢查電腦上是否存在MS17-010的漏洞,另外就是檢查電腦上的SMB v1是否關閉,如呈現開啟,亦可協助用戶停用SMB v1。若是企業用戶,最好先與IT管理人員確認,公司電腦是否須利用此工具關閉SMBv1(像是有可能導致公司電腦遇到無法使用列印功能的情形)。
同時他們表示,近日又偵測到另一新勒索蠕蟲變種「UIWIX」,同樣也是利用Server Message Block(SMB)漏洞EternalBlue(亦被稱為CVE-2017-0144和MS17-10)以執行擴散行為,甚至他們認為比WannaCry更加狡猾且不留痕跡,提醒使用者不該就此鬆懈。

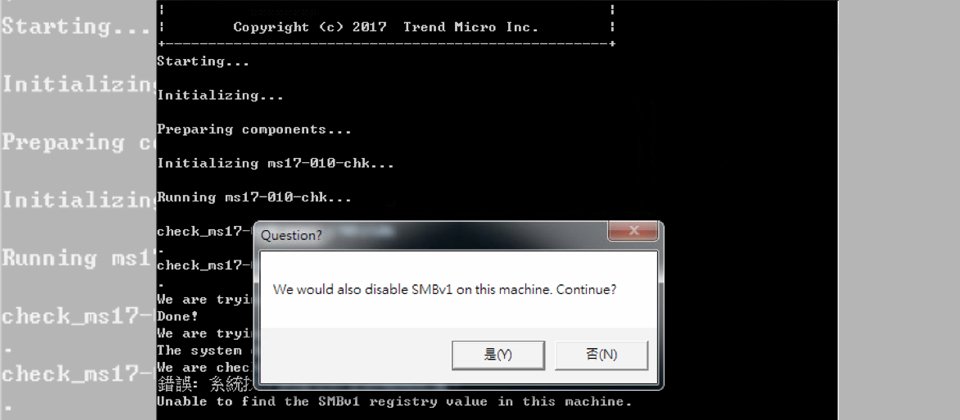
在執行Trend Micro WCRY Simple Patch Validation Tool後,若電腦已完成MS17-010相關更新,會出現以上訊息,讓使用者快速知道這臺電腦,已經完成WannaCry必裝的Windows安全更新套件。
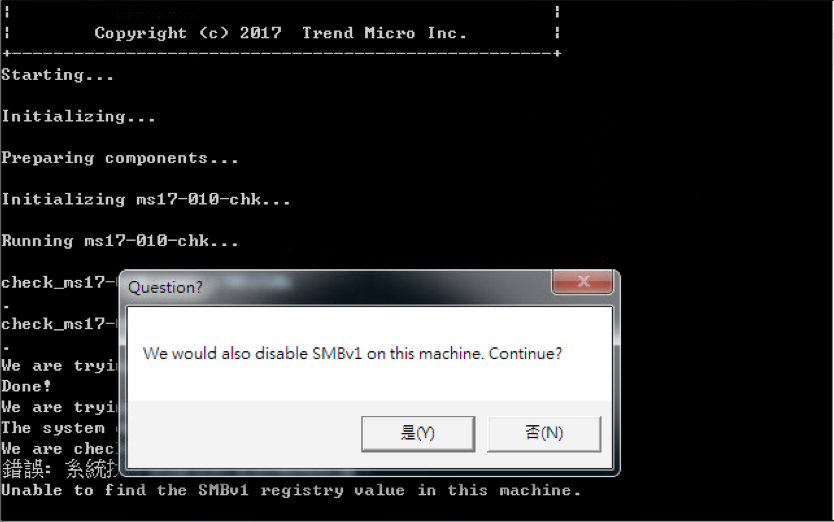
另外,該程式若發現電腦上的SMB v1呈現開啟,也將會詢問用戶是否要停用SMB v1。
使用Nmap針對WannaCry檢測的Scripts範本
企業網管人員可將下方純文字內容存成smb-vuln-ms17-010.nse檔,有能力的人亦可參考Github上的文件自行修正
local smb = require "smb"
local vulns = require "vulns"
local stdnse = require "stdnse"
local string = require "string"
description = [[
Attempts to detect if a Microsoft SMBv1 server is vulnerable to a remote code
execution vulnerability (ms17-010).
The script connects to the $IPC tree, executes a transaction on FID 0 and
checks if the error "STATUS_INSUFF_SERVER_RESOURCES" is returned to
determine if the target is not patched against ms17-010.
Tested on a vulnerable Windows 7. We might have some issues with v2 protocols with
signing enabled.
References:
* https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
* https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
* https://msdn.microsoft.com/en-us/library/ee441489.aspx
* https://github.com/rapid7/metasploit-framework/blob/master/modules/auxiliary/scanner/smb/smb_ms17_010.rb
]]
---
-- @usage nmap -p445 --script smb-vuln-ms2017-010 <target>
-- @usage nmap -p445 --script vuln <target>
--
-- @output
-- Host script results:
-- | smb-vuln-ms17-010:
-- | VULNERABLE:
-- | Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
-- | State: VULNERABLE
-- | IDs: CVE:CVE-2017-0143
-- | Risk factor: HIGH
-- | A critical remote code execution vulnerability exists in Microsoft SMBv1
-- | servers (ms17-010).
-- |
-- | Disclosure date: 2017-03-14
-- | References:
-- | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
-- | https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
-- |_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
--
-- @xmloutput
-- <table key="CVE-2017-0143">
-- <elem key="title">Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)</elem>
-- <elem key="state">VULNERABLE</elem>
-- <table key="ids">
-- <elem>CVE:CVE-2017-0143</elem>
-- </table>
-- <table key="description">
-- <elem>A critical remote code execution vulnerability exists in Microsoft SMBv1
 servers (ms17-010).
</elem>
-- </table>
-- <table key="dates">
-- <table key="disclosure">
-- <elem key="month">03</elem>
-- <elem key="year">2017</elem>
-- <elem key="day">14</elem>
-- </table>
-- </table>
-- <elem key="disclosure">2017-03-14</elem>
-- <table key="refs">
-- <elem>https://technet.microsoft.com/en-us/library/security/ms17-010.aspx</elem>
-- <elem>https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143</elem>
-- <elem>https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/</elem>
-- </table>
-- </table>
---
author = "Paulino Calderon <paulino()calderonpale.com>"
license = "Same as Nmap--See https://nmap.org/book/man-legal.html"
categories = {"vuln", "safe"}
hostrule = function(host)
return smb.get_port(host) ~= nil
end
local function check_ms17010(host, port, sharename)
local status, smbstate = smb.start_ex(host, true, true, sharename, nil, nil, nil)
if not status then
stdnse.debug1("Could not connect to '%s'", sharename)
return false, string.format("Could not connect to '%s'", sharename)
else
local overrides = {}
local smb_header, smb_params, smb_cmd
stdnse.debug1("Connected to share '%s'", sharename)
overrides['parameters_length'] = 0x10
--SMB_COM_TRANSACTION opcode is 0x25
smb_header = smb.smb_encode_header(smbstate, 0x25, overrides)
smb_params = string.pack(">I2 I2 I2 I2 B B I2 I4 I2 I2 I2 I2 I2 B B I2 I2 I2 I2 I2 I2",
0x0, -- Total Parameter count (2 bytes)
0x0, -- Total Data count (2 bytes)
0xFFFF, -- Max Parameter count (2 bytes)
0xFFFF, -- Max Data count (2 bytes)
0x0, -- Max setup Count (1 byte)
0x0, -- Reserved (1 byte)
0x0, --Flags (2 bytes)
0x0, --Timeout (4 bytes)
0x0, --Reserved (2 bytes)
0x0, --ParameterCount (2 bytes)
0x4a00, --ParameterOffset (2 bytes)
0x0, --DataCount (2 bytes)
0x4a00, -- DataOffset (2 bytes)
0x02, -- SetupCount (1 byte)
0x0, -- Reserved (1 byte)
0x2300, -- PeekNamedPipe opcode
0x0, --
0x0700, --BCC (Length of "\PIPE\")
0x5c50, --\P
0x4950, --IP
0x455c --E\
)
stdnse.debug2("SMB: Sending SMB_COM_TRANSACTION")
result, err = smb.smb_send(smbstate, smb_header, smb_params, '', overrides)
if(result == false) then
stdnse.debug1("There was an error in the SMB_COM_TRANSACTION request")
return false, err
end
result, smb_header, _, _ = smb.smb_read(smbstate)
_ , smb_cmd, err = string.unpack("<c4 B I4", smb_header)
if smb_cmd == 37 then -- SMB command for Trans is 0x25
stdnse.debug1("Valid SMB_COM_TRANSACTION response received")
--STATUS_INSUFF_SERVER_RESOURCES indicate that the machine is not patched
if err == 0xc0000205 then
stdnse.debug1("STATUS_INSUFF_SERVER_RESOURCES response received")
return true
end
else
stdnse.debug1("Received invalid command id.")
return false, err
end
end
end
action = function(host,port)
local vuln_status, err
local vuln = {
title = "Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)",
IDS = {CVE = 'CVE-2017-0143'},
risk_factor = "HIGH",
description = [[
A critical remote code execution vulnerability exists in Microsoft SMBv1
servers (ms17-010).
]],
references = {
'https://technet.microsoft.com/en-us/library/security/ms17-010.aspx',
'https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/'
},
dates = {
disclosure = {year = '2017', month = '03', day = '14'},
}
}
local sharename = stdnse.get_script_args(SCRIPT_NAME .. ".sharename") or "IPC$"
local report = vulns.Report:new(SCRIPT_NAME, host, port)
vuln.state = vulns.STATE.NOT_VULN
vuln_status, err = check_ms17010(host, port, sharename)
if vuln_status then
stdnse.debug1("This host is missing the patch for ms17-010!")
vuln.state = vulns.STATE.VULN
else
if nmap.verbosity() >=1 then
return err
end
end
return report:make_output(vuln)
end |
熱門新聞
2026-02-09
2026-02-10
2026-02-06
2026-02-10
2026-02-10
2026-02-09
2026-02-10