這十多年來,企業與政府組織日益重視資安,ISO 27001系列相關的國際通用驗證標準,以及相關制度,逐漸成為主流的資訊安全架構,值得關注的是,這系列標準可能在接下來兩三個月後,就有新版發布。
基本上,現行國際資安標準ISO 27001:2013,是在2013年10月推出的,距今有8年之久,而更前一次發布則是2005年。
簡單來說,ISO 27001:2013是可被實際驗證的國際資安管理標準, 訂定ISMS管理制度面的要求,至於另一套ISO 27002:2013,是完全對應ISO 27001:2013的附錄A,作用在於使兩者保持一致,可針對附錄A的控制要求,給予最佳實踐方式,提供完整且具體的指引參考。
隨著全球威脅局勢轉變,資安管理標準也要合乎時宜,因此,早在2018年3月,ISO國際標準組織就已啟動相關改版計畫。
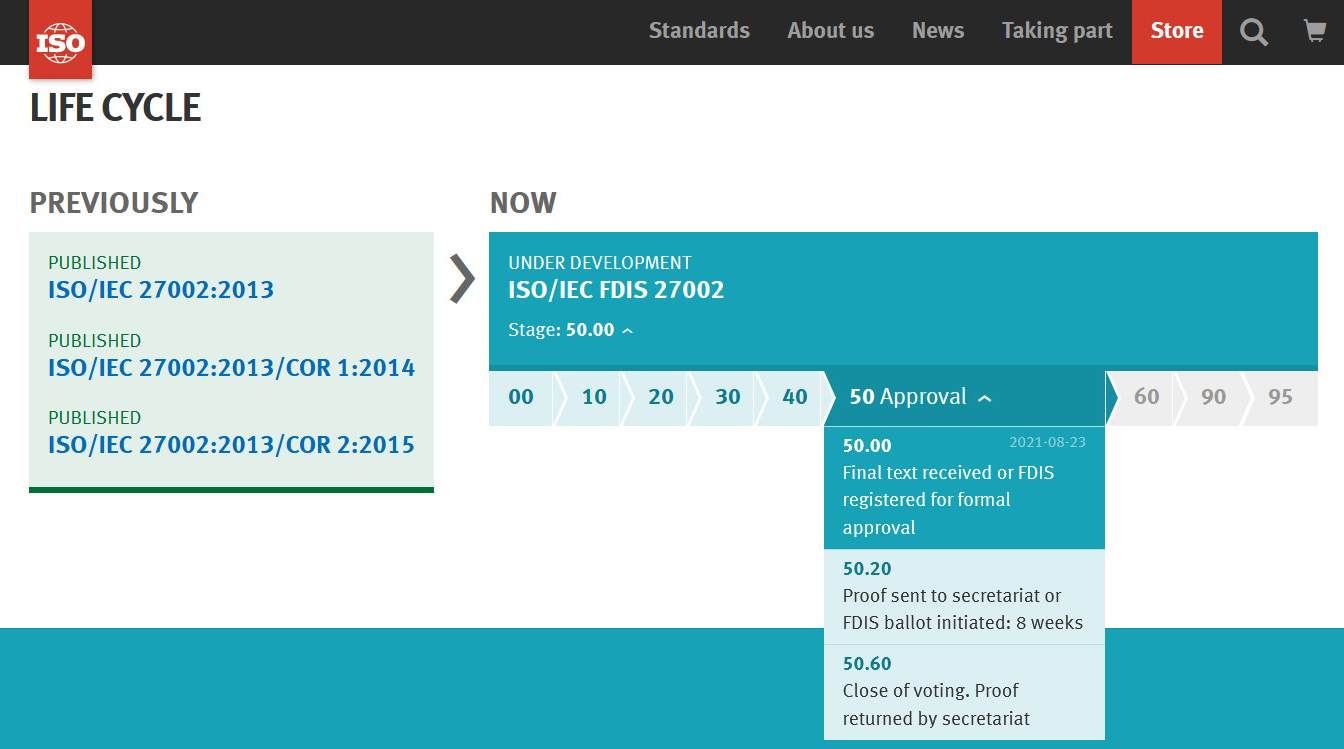
今年這項計畫有了明顯的進展。在4月23日,新版ISO 27002國際標準草案(DIS版)完成投票,到了8月23日,最終草案版本開始登記。
目前可確定的是,新版ISO 27002進度接近尾聲,現將等待進行最終草案版本的投票,而投票啟動後還需要8周,之後將明定為最終草案版本,再進入最後標準發布程序。
儘管驗證標準ISO 27001的改版時程,在ISO官方網站上仍未有消息,但相關動作仍意謂著,ISO 27001/ISO 27002新版本發布時程,已經離現在不遠。
目前ISO 27002改版進度較明確,已於8月23日開始登記,接下來就會進行投票,大約兩三個月後,也就是明年初就會確定公布,整體改版時程歷經近4年。至於ISO 27001的改版,最近在10月也傳出將開始討論會議,但多久能完成改版,需視改版幅度而定。
標準名稱將有變動,擴大資安控制範圍並從標題刪除實踐準則一詞
關於這次改版的內容,在國際組織ISO官方網站上,已有透露相關資訊。例如,在其公布的ISO 27002草案版本中,從名稱來看,新版ISO 27002就有很大不同。
以ISO 27002:2013為例,現行版本的名稱是:「資訊科技—安全技術—資訊安全控制實施準則」,未來,將變成「資訊安全、網路安全及隱私保護—資訊安全控制」。
特別的是,「實踐準則」將從標題中刪除,因為,ISO希望27002的存在,能更妥善反映其作為資安控制參考的目的。ISO指出,所欲達成的目的並未改變,都是為了幫助組織做好資安控制,確保組織不會忽視任何必要的控制。而且,這些針對個別控制措施的指引,仍是基於國際公認的資安最佳實踐。
在ISO 27002新版草案中,歸納4大資安控制類型,包括組織、人員、實體與技術
值得關注的是,依據新版草案來看,關於資安控制措施類別,將重新分為4大類別。具體而言,包括:第五章的組織控制(Organization Controls),從5.1到5.37的章節當中,總共有37項控制措施;第六章人員控制(People Controls),有8項控制措施;第七章實體控制(Physical Controls),有14項控制措施;第八章技術控制(Technological Controls),有34項控制措施。因此,總共會有4大類別與93項控制措施。
同時ISO也提及,此標準文件的結構會有所改變,將使用簡單的分類法來呈現控制措施。
整體而言,從ISO公布的草案版本章節名稱,各界可看出這次改版的一些變化,包括:合併部分控制措施,甚至予以刪除,也增加了多項新的控制措施。由於改版還在進行中,後續我們也將持續關注相關變化。
ISO 27002新版草案(DIS)版本章節概覽
| 5 | 0rganizational controls | 7 | Physical controls |
| 5.1 | Policies for information security | 7.1 | Physical security perimeter |
| 5.2 | Information security roles and responsibilities | 7.2 | Physical entry controls |
| 5.3 | Segregation of duties | 7.3 | Securing offices, rooms and facilities |
| 5.4 | Management responsibilities | 7.4 | Physical security monitoring |
| 5.5 | Contact with authorities | 7.5 | Protecting against physical and environmental threats |
| 5.6 | Contact with special interest groups | 7.6 | Working in secure areas |
| 5.7 | Threat intelligence | 7.7 | Clear desk and clear screen |
| 5.8 | Information security in project management | 7.8 | Equipment siting and protection |
| 5.9 | Inventory of information and other associated assets | 7.9 | Security of assets off-premises |
| 5.10 | Acceptable use of information and other associated assets | 7.10 | Storage media |
| 5.11 | Return of assets | 7.11 | Supporting utilities |
| 5.12 | Classification of information | 7.12 | Cabling security |
| 5.13 | Labelling of information | 7.13 | Equipment maintenance |
| 5.14 | Information transfer | 7.14 | Secure disposal or re-use of equipment |
| 5.15 | Access control | 8 | Technological controls |
| 5.16 | Identity management | 8.1 | User endpoint devices |
| 5.17 | Authentication information | 8.2 | Privileged access rights |
| 5.18 | Access rights | 8.3 | Information access restriction |
| 5.19 | Information security in supplier relationships | 8.4 | Access to source code |
| 5.2 | Addressing information security within supplier agreements | 8.5 | Secure authentication |
| 5.21 | Managing information security in the ICT supply chain | 8.6 | Capacity management |
| 5.22 | Monitoring, review and change management of supplier services | 8.7 | Protection against malware |
| 5.23 | Information security for use of cloud services | 8.8 | Management of technical vulnerabilities |
| 5.24 | Information security incident management planning and preparation | 8.9 | Configuration management |
| 5.25 | Assessment and decision on information security events | 8.10 | Information deletion |
| 5.26 | Response to information security incidents | 8.11 | Data masking |
| 5.27 | Learning from information security incidents | 8.12 | Data leakage prevention |
| 5.28 | Collection of evidence | 8.13 | Information backup |
| 5.29 | Information security during disruption | 8.14 | Redundancy of information processing facilities |
| 5.30 | ICT readiness for business continuity | 8.15 | Logging |
| 5.31 | Identification of legal, statutory, regulatory and contractual requirements | 8.16 | Monitoring activities |
| 5.32 | Intellectual property rights | 8.17 | Clock synchronization |
| 5.33 | Protection of records | 8.18 | Use of privileged utility programs |
| 5.34 | Privacy and protection of PlI | 8.19 | Installation of software on operational systems |
| 5.35 | Independent review of information security | 8.20 | Network controls |
| 5.36 | Compliance with policies and standards for information security | 8.21 | Security of network services |
| 5.37 | Documented operating procedures | 8.22 | Web filtering |
| 6 | People controls | 8.23 | Segregation in networks |
| 6.1 | Screening | 8.24 | Use of cryptography |
| 6.2 | Terms and conditions of employment | 8.25 | Secure development lifecycle |
| 6.3 | Information security awareness, education and training | 8.26 | Application security requirements |
| 6.4 | Disciplinary process | 8.27 | Secure system architecture and engineering principles |
| 6.5 | Responsibilities after termination or change of employment | 8.28 | Secure coding |
| 6.6 | Confidentiality or non-disclosure agreements | 8.29 | Security testing in development and acceptance |
| 6.7 | Remote working | 8.30 | Outsourced development |
| 6.8 | Information security event reporting | 8.31 | Separation of development, test and production environments |
| 8.32 | Change management | ||
| 8.33 | Test information | ||
| 8.34 | Protection of information systems during audit and testing |
資料來源:ISO,iThome整理,2021年10月
熱門新聞
2026-02-11
2026-02-11
2026-02-09
2026-02-10
2026-02-10
2026-02-06
2026-02-10